5. Identification and authentication
Definition
Authentication, also called "verification" is the capability to answer the following question:
- is this person who he or she claims to be?
- Is this object what it claims to be?
Authentication and identification functions refers to:
- Authenticating a user or object upon connection to a system (that can be complex)
- Making sure that during the whole time if his her or its connection it is still the same person or object
- Limiting and checking the rights of this user or object within the system she / he / it is connected to, and between users / objects (e.g. this doctor can enable the update of the firmware of this device type for these patients...)
- optionally securing the transactions and data exchanged between the connected user or object, and the system it is connected to.
Also, the Identity and authentication management shall take care of defining which users and objects can connect to the system (e.g. add or delete user, recognize an object that is trying to connect...) and modify his, her or its rights (this can be done by administrator but also by other users)
Objectives of the topic session
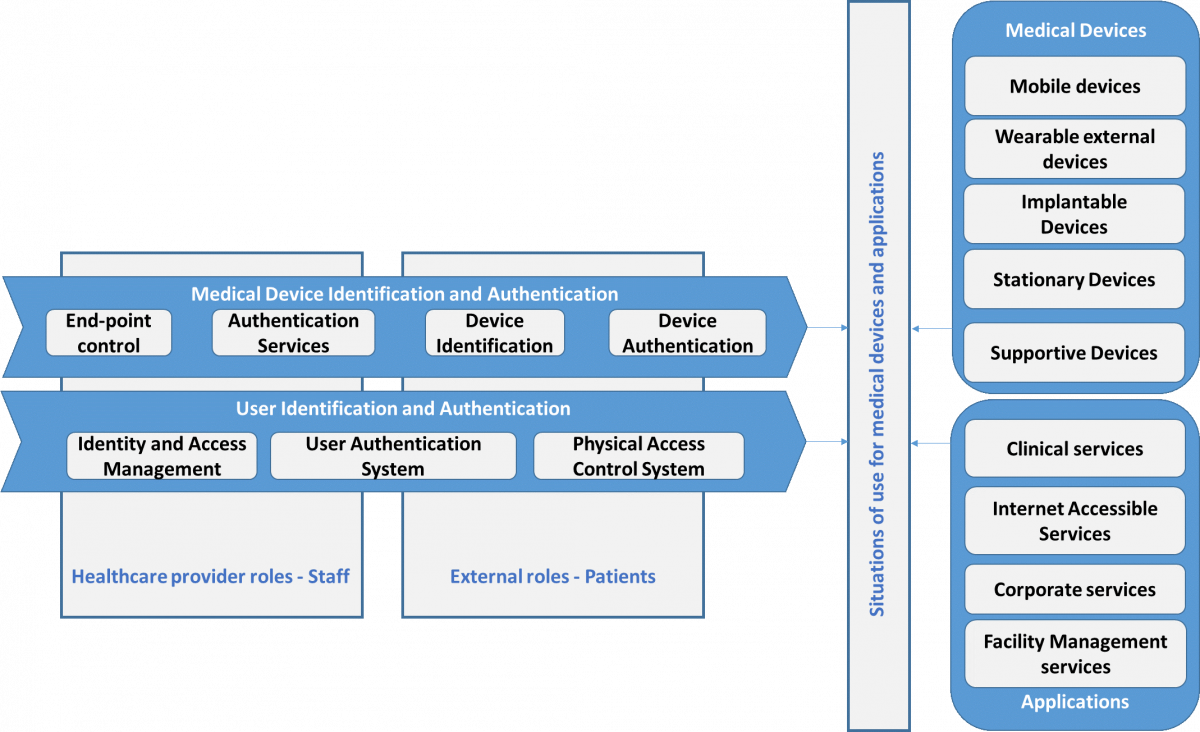
In order to collect the requirements, we go through a matrix crossing seven Identification and Authentication functions with the two broad types of “objects” to be identified and authenticated: Medical Devices and Users.
We also consider that different solutions may be required depending on
- the work role of the user
- the type of application a user interacts
- the type of medical device a user interacts
- the situation related to how a medical device is used (e.g. the same medical device may connect to multiple hospital systems, medical devices are directly talking to each other).